March 3, 2022 by Gabriel Bassett
Introducing Attack Flow: Graphs for Infosec
IT’S FINALLY HERE! A project I’ve put a decade of experience into and months of work along with experts at @MITREengenuity CTID and other contributing organizations: ATTACK FLOW! https://github.com/center-for-threat-informed-defense/attack-flow & https://github.com/vz-risk/flow.
Wanna know more? Read on!
It’s been clear for a long time that atomic infosec wasn’t cutting it. We need to be able to describe graphs of actions attackers take. (Flows so to speak.) But we lacked a common language to express them. Attack Flow provides that language using the 3C’s: Complexity, Causality, and Context:
- Complexity means relationships between more than two ’things'.
- Causality means the causal sequence of actions and it’s change to system state
- Context means all the descriptive details
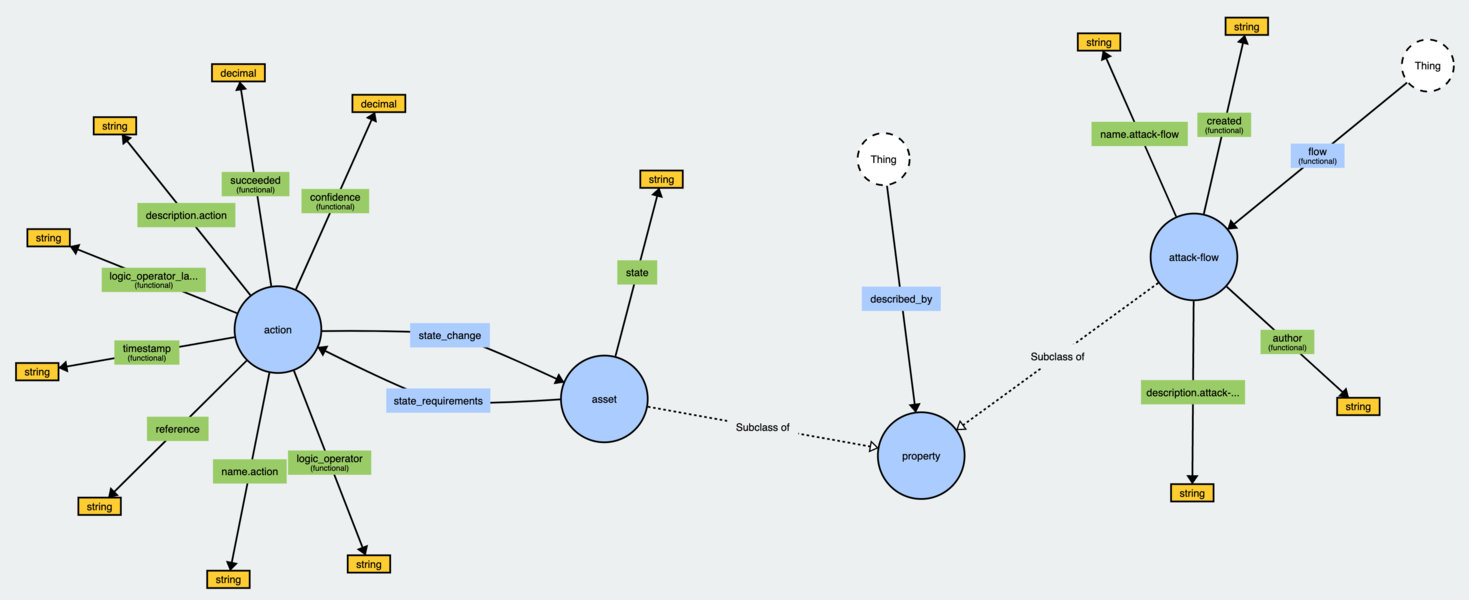
Attack Flow has 4 parts: Actions, Assets, Properties (Objects/Data) & Relationships, all joined through a Flow.
- Actions are things that happen
- Assets are things that have state changes
- Properties are contextual triples (X -[Property of]-> Y) describing either other ’things’ or data like a hash
- Relationships create the causal connections
- Flows are the set of Actions, Assets, Properties, and Relationships
Almost any use case in information security can benefit from Attack Flows!
- Let’s say you have you’re conducting DFIR and want to document the actions the attacker took and the artifacts you based your documentation on. YOU CAN DO THAT!
- Or you want a structured way to share the path an attack took. YOU CAN DO THAT!
- You want to write detection signatures associated with attackers taking multiple actions? YOU CAN DO THAT!
- You want to simulate attacks so you can tell if those rules are working? YEP. THAT TOO!
- You want to aggregate attacks and query to see what paths attackers often take? CAN DO!
- You want to communicate about your attack surface to leadership? SURE!
- You want to document pen tests and red teaming so it’s repeatable for retest or secops training? ABSOLUTELY!
You want Attack Flow to be your single pane of glass? It won’t do that. It’s a schema not a platform. Which gets to the next step: Building workflows for the use cases and incorporating it into tools.
If this sounds like something you might be interested in, the next step is reading up at the two repos above. https://github.com/center-for-threat-informed-defense/attack-flow is CTID’s documentation of the schema while https://github.com/vz-risk/flow is the DBIR team’s implementation as linked data.
The reality is this is very new and will likely leave you with more questions than answers. REACH OUT! I can help! This has been a goal of mine since I met with Blake Strom (then at Mitre) and Stephan Chenette (AttackIQ) at RSA over half a decade ago!
With Attack Flow we can now graph together!